Many engineering teams know the struggle of facing down an angry business leader looking to deliver something incomplete to meet a deadline under the pretense of delivering an MVP and “not boiling the ocean“. The struggle and challenge is usually driven by these actors with these real considerations
- The engineers want to make sure they deliver something of quality and usable and want to avoid business types from trading off quality for profit
- The project managers want to meet deadlines
- The business leaders want to bill progressively and avoid over engineering and runway project cost and timelines
Allow me to attempt to set some of rules for our thinking about MVPs so that we can try and find the right win/win for the actors above.
#1 – MVP does not mean what you think it does
As Yevgeniy (Jim) Brikman of Ycombinator writes in this important article;
“It’s the same story again and again. First, a team comes up with an idea. Next, they build a minimum viable product (MVP) as a proof of concept, spending a lot of time arguing about which features to include or exclude from the MVP. Finally, if the MVP works well, they plan on building the full, mature, stable product.
So what’s wrong with this picture? Why does it all go wrong for so many startups?
The problem is that these teams do not understand the point of an MVP. An MVP is not just a product with half of the features chopped out, or a way to get the product out the door a little earlier. In fact, the MVP doesn’t have to be a product at all. And it’s not something you build only once, and then consider the job done.”
MVP is not a compromise you make to rush a minimally acceptable product out the door to meet a timeline but an experiment to test your riskiest assumptions so that the product your building stays true to the reality of the market and the users you are trying to reach. He further explains;
“An MVP is a process that you repeat over and over again: Identify your riskiest assumption, find the smallest possible experiment to test that assumption, and use the results of the experiment to course correct. When you build a product, you make many assumptions. You assume you know what users are looking for, how the design should work, what marketing strategy to use, what architecture will work most efficiently, which monetization strategy will make it sustainable, and which laws and regulations you have to comply with. No matter how good you are, some of your assumptions will be wrong. The problem is, you don’t know which ones.
Please do read the rest of this excellent article on Ycombinator
#2 – Whatever you deploy and deliver, must be usable at all times
The picture below done by Henrik Kniberg explains it all better than words;
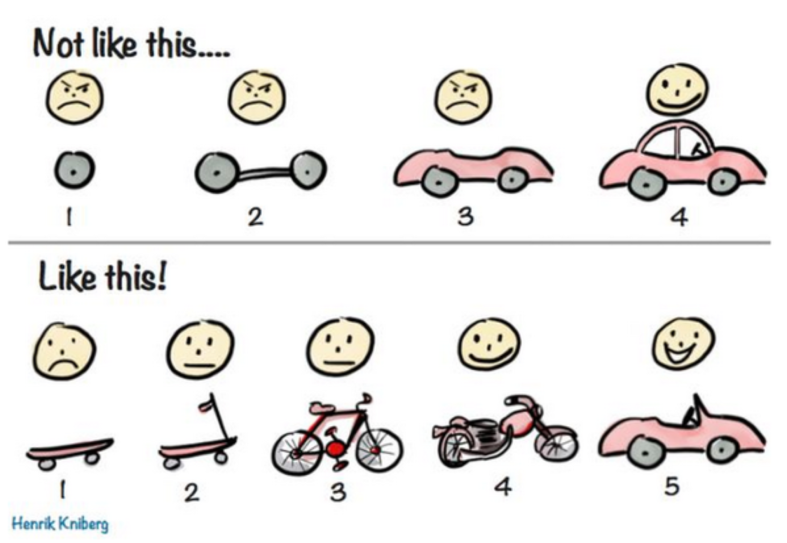
There is a very nice explanation of this image from Henrik Kniberg on the Crisp consultant’s blog.
It is ok to stagger deployment, to break things down to milestones constrained by resources and economic considerations, but at every step of the way, the product must be usable and of a baseline quality.
#3 – The Airbnb 100 people love rule for quality
Brian Chesky, founder of Airbnb is famous for his 100 people love rule;
“The best piece of advice I ever got was from our first investor, Paul Graham. He said it’s better to have 100 people love you than a million people that sort of like you, so if you can find 100 people that love your product — as long as there are more people like them in the world — then you have an idea that I believe will spread around the world. But if you can’t get 100 people who absolutely love your product, then you do have a problem.”
Therefore rules #2 and #3 tell us we should focus on staggering our steps and milestones to deliver steps that qualitatively reach fans and focus on slowly growing that fan base.
It is better to be focused on delivering higher quality to less people than lower quality to more people – if retention of users and the creation of fans is important to your overall business objectives.
#4 – Embracing Agile
The assumption behind the whole concept of MVP is that you are working on an agile methodology and not waterfall. Agile is all about breaking down the challenge to smaller steps that allow for better empowerment of small multidisciplinary teams to apply creativity to solving those challenges, about being more customer centric and consultative and about seeing solutions in more scenario based architectures then component based ones.
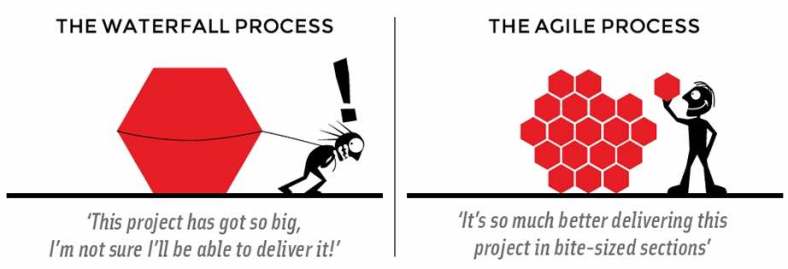
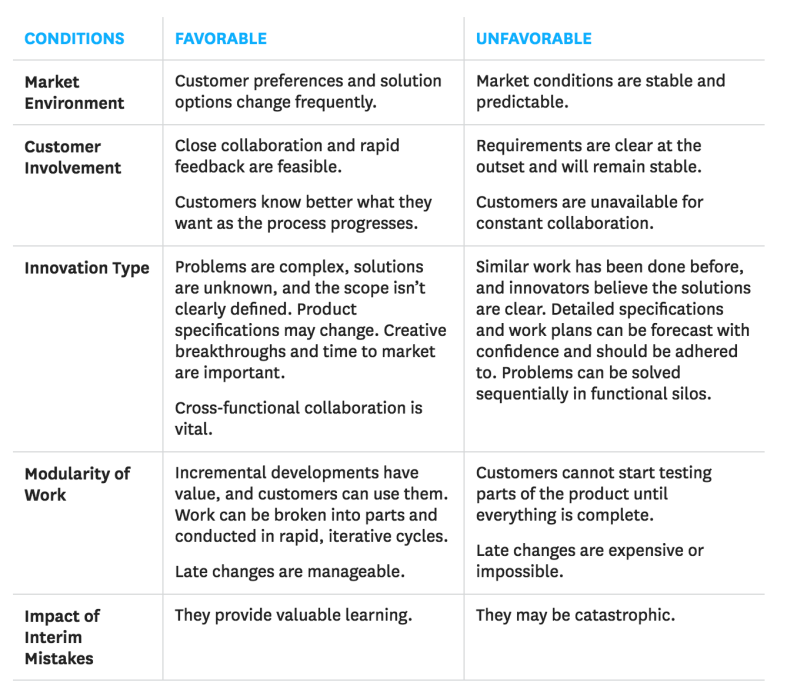
Harvard Business Review sums up the challenges and opportunities of embracing agile here and even throws in this useful diagram of what situations work best with agile and what does not;
#5 – Quality means planning for failure
Netflix and it’s simian army has taught us the art and science of planning for failure ;
“The cloud is all about redundancy and fault-tolerance. Since no single component can guarantee 100% uptime (and even the most expensive hardware eventually fails), we have to design a cloud architecture where individual components can fail without affecting the availability of the entire system. In effect, we have to be stronger than our weakest link. We can use techniques like graceful degradation on dependency failures, as well as node-, rack-, datacenter-/availability-zone-, and even regionally-redundant deployments. But just designing a fault tolerant architecture is not enough. We have to constantly test our ability to actually survive these “once in a blue moon” failures.”
and today we have mature best practises for failure mapping and tools for planning for failure. Every application should also be designed for graceful degradation.
#6 – The importance of being timely
If we agree on #1 to #5, we now need a reminder as builders that you can miss an opportunity if you take to long. That annoying business leader has a point, a company can miss an opportunity because it’s builders took too long.



 AI to assist and monitor the human agents
AI to assist and monitor the human agents